Disasters come in many forms. We always talk about hurricanes, tornadoes, floods and fires, but they could be anything, as small a cup of coffee accidentally spilled across a laptop keyboard. The reality is that you need to prepare for as many potential problems as possible. This is particularly true when every minute of downtime can cost you thousands: ITIC’s latest survey data finds that 98% of organizations say a single hour of downtime costs over $100,000.
Creating a backup and disaster recovery (BDR) plan is a complicated venture, requiring a deeper understanding of your technology than you may be used to. We want to help you break down some of that complexity by giving you our 25 essential components for your backup and disaster recovery plan, whether they are steps, assignments or measures for creative thinking.
 Preventative Measures
Preventative Measures
Speaking broadly, avoiding disaster is always your best bet. When you are addressing preventative measures, you are taking into consideration all elements that could potentially lead to disaster. Whether you have daisy-chained power cords or your server room has no door lock, this preemptive attack on impending problems can save you a ton of work down the road. Take a walk around your office with prevention in mind. Look for unlocked computers and suspect cabling. Set up password requirements and two-factor authentication. This is the common sense part of prevention, and it’s never too early to start. (But, there is definitely a too-late.)
 Detective Measures
Detective Measures
How would you go about uncovering more complicated problems? Do you have the capacity to do such a thing? Detective measures are not in reference to Sam Spade’s tailor. These are ongoing efforts to uncover problems that are not surface level. Think of this as your neighborhood watch. It is a process of determining suspect protocols.
 Corrective Measures
Corrective Measures
Your corrective measures are your BDR plan. How will you react to problems and challenges across the board? This is your recovery, and your business relies on its expediency. Time is money, so the more efficient your corrective measures, the faster you get back to work.
Corrective measures should involve policies and procedures for a wide variety of circumstances. Likewise, they should help you determine recovery roles for executives and managers across your organization. Always think of your BDR plan as a community affair within your business.
Source: Aberdeen Essentials
 Determine Recovery Time Objective
Determine Recovery Time Objective
What’s the maximum time that you can be offline? Is it a week of downtime? A day? An hour? Your recovery time can make or break your organization. Your BDR plan, therefore, should be designed around hitting your recovery time objective (RTO). The sooner your team is back to normal, the better. Depending on your type of backup, you could be looking at hours, even days down. Determine what is the maximum your business can be down, and work backward from there.

5
Determine Recovery Point Objective
What’s the maximum time your data can be unreachable? In effect, your recovery point objective (RPO) helps you parcel your recovery. Are there pieces of data you need sooner than others? You can prioritize your recovery to help you get back to the essentials sooner. If your team is forced to work outside the office, your RPO gives priority to your business applications, so they can get back to functionality.
 Plan for Scalability
Plan for Scalability
Growth, of course, is the ultimate goal of business. Knowing that scalability is ideal, you want to prepare your BDR to reflect that. This could be targeted toward hardware, software or people. You never want to be in a situation where your BDR plan has a shortfall in access to data, software licenses, laptop and desktop replacements, and so on.
Plan for scalability, using growth estimates for the next three to five years. While your BDR plan should be a living document, you want to be able to anticipate your organization’s growth. Your business goals should, therefore, be reflected in the BDR plan.
 Check Physical Security
Check Physical Security
Part of any good BDR plan is ensuring physical security. Not the physical security of your staff, but rather of the office equipment itself. This could be computers, phones, servers and more. In the circumstance that the office is temporarily on lockdown, you need to ensure that workstations are on lockdown and equipment is secure. You never want to replace any more equipment than you have to.
 Check Network Security
Check Network Security
Your standard cybersecurity practices keep your business safe. This includes firewalls, antivirus and other elements. When a disaster strikes, you want to ensure that those best practices are held strong, even if you must temporarily work out of the office. By keeping track of your cybersecurity best practices, you can create carryover protocols that keep those best practices in check, even during periods of remote working.
When creating your network security program, ensure your solutions are securely transferable to remote locations.
 List Software Components
List Software Components
What apps do you require for your business to run? For most businesses, reliance on a handful of apps is commonplace. After a disaster, you want to know all the software that your team uses and how to effectively get them back online. This practice also gives you the opportunity to keep your team on streamlined software. After all, the fewer platforms you require, the easier recovery becomes.
Not only should you list your software components, but you should prioritize them. If the bulk of your staff requires access to Salesforce to be productive, for example, then it should be listed as a priority.
 Determine Facilities
Determine Facilities
Where will your business operate if you can’t work from the office? Do you have a business recovery site? You never want to wait until after a disaster, when every minute of downtime works against you, to start identifying temporary office spaces. By knowing exactly what you need in a variety of situations, you can plan for quick access to locations.
Let’s imagine, a flood in the building floor above your office has found its way into your server room and walls over the weekend. Water damage has ruined the server equipment, caused shorts in the walls that have rendered connected desktops useless, and left your floors in a layer of sitting water. Can your team work remotely, from home, or do you need to provide equipped facilities? Determine how many workstations you need, how you will recover your backup data, will you need a temporary phone system, and how long will you be there. Having a few location options that can give you quick access after a disaster is a first step in being prepared for recovery.
 Clarify Bandwidth
Clarify Bandwidth
Tied in with your facilities, you need very real numbers on your bandwidth. If you have a small business of 25 people, but you use a lot of bandwidth, you need your facilities to be able to meet your peak load. You can look at your internet bill and get a general sense over a few months of the kind of bandwidth your team uses. From there, as you shop temporary office spaces, you can make sure you have the necessary internet requirements to keep your team working.
 Automate Backups
Automate Backups
Obviously, backups are the backbone of your recovery. It’s imperative that you take frequent backups, but more specifically, you need to automate your backups. Automation of backups is the only way to ensure you get the frequency and accuracy you need. If you can automate as frequently as every 15 minutes, you’ve effectively minimized the data loss you could experience to the bare minimum.
 Ensure Redundancy
Ensure Redundancy
Redundancy is your safety net and is the powerhouse of your backup procedure. This can be accomplished in multiple ways, through on-premise, cloud-based or hybrid techniques. By scattering backups, you can cover multiple disaster scenarios. On-premise backups can cover you in the case of connection issues, but cloud-based backups deliver greater mobility when having to resume operations from an off-site temporary location
 Harden Your Cybersecurity
Harden Your Cybersecurity
A key to having a secured recovery is having a secure baseline. By implementing the proper cybersecurity procedures, you not only mitigate risk and thwart potential disaster from a data loss perspective, but likewise, you ensure your backups have that same protection. Think of a ransomware attack. Many attacked businesses are forced to pay the ransom to retrieve their kidnapped data. With protected backups, you can reboot smoothly and efficiently, so you never have to play the ransom game.
Source: Cybersecurity Ventures
 Do Your Compliance Due Diligence
Do Your Compliance Due Diligence
Just because a disaster strikes doesn’t mean you can be lax in your regulatory compliance measures. Hackers look for opportunities of weakness, and a business disaster could supply that opportunity. Ensure your protection of customer data stays strong during a recovery period. Whether this is setting protocols to follow regulatory compliance or doing your due diligence to protect your client information, verify you’ve got the tools in place to let your security carry you through the recovery period.
 Keep Licenses Current
Keep Licenses Current
Maintaining proper licensure with your software and business apps is crucial, not only from a day-to-day perspective but also when it comes to speedy recovery. When you’re trying to recover, you need your software up and running as fast as possible. Keep a log of all your software licenses so that reboot is simple and efficient. You never want to be stuck in a position where certain staff members are locked out of workflow, simply because their software is out of date.
 Establish Key Players
Establish Key Players
Your people are essential to the recovery of your business. In that sense, they must be part of your backup and disaster recovery plan. In your plan, you need to establish key players and delegate responsibility so the task of recovery isn’t dependent on a single person. Assign roles so that in an emergency you know certain aspects are taken care of without the need for direct orders and management. Start with communication channels, because your first order of business is to make sure everyone is safe (in a larger disaster) and to keep everyone in touch throughout recovery.
 Create BYOD Program
Create BYOD Program
Contact during a disaster is paramount. Many organizations are blindsided during, say, bad weather days. But by creating a bring-your-own-device program, you can keep your staff communicating wherever they. With BYOD as part of their day-to-day operations, then off-site communication will be second nature to your team.
Source: Bureau of Labor Statistics
 Create Scenarios
Create Scenarios
The motto of the Coast Guard is semper paratus or “always ready.” The way to achieve preparedness is to anticipate potential actions. By creating scenarios, you can anticipate causes and create the effect. From natural disasters to coffee in a keyboard, you need to cover as many scenarios as possible, so that your team’s reaction is not paralysis by analysis. Plan for multitudes and practice, practice, practice.
 Employ Cloud-Based Software
Employ Cloud-Based Software
As much as possible, you should use SaaS. Software-as-a-service can offer huge benefits to your day-to-day operations, but likewise, it can give you some of the quickest turnarounds after a disaster. With many cloud-based software services, you essentially leave your workload in an offsite data center. Not only is this great for redundancy, but it gives enterprise-level cybersecurity and network strength.
Source: Gartner
 Prioritize Restoration
Prioritize Restoration
Restoration should in its own way have an org chart. Ideally, this lists not only the priorities of your recovery based on software and tools, but also can be departments or groups of people. If you have some 24/7 service offering that is the number one feature of your services, then getting that team and those tools restored is first priority after a disaster. Because recovery always takes some element of time, you must prioritize restoration.
 Consider Virtualization
Consider Virtualization
Much of backup and recovery depends on the simplicity of your system. This often boils down to the architecture. Desktop virtualization is one of those tools that helps you simplify your architecture, even in the most complex network structures. Essentially, it creates virtual desktop space for an employee to log into. If a machine is destroyed in some way, with desktop virtualization, a simple login from a new computer gives you total, immediate access to everything the old computer had.
 Monitor Tests and Usage
Monitor Tests and Usage
Part of your larger security practices should be monitoring usage. Who is truly accessing your system? Do you have the tools in place to see who enters your system, who has access to levels of data? The right software tools can help you monitor usage and traffic into your system. Likewise, you can monitor the frequency and strength of your backup testing. Awareness is everything when it comes to recovery.
 Test, Test, Test
Test, Test, Test
Ideally, you take an automated backup every 15 minutes. But how do you know that your backup will work when the time comes? The only true method is with testing. You have to test frequently so you always know your backups will hold true. Many businesses who face failed backups thought they were functioning. You have to test and test frequently.
 Get Ongoing BDR Support
Get Ongoing BDR Support
A good, effective BDR plan is what’s going to give you quick recovery. At Axxys Technologies, we have a long history of designing, testing and delivering ongoing support for backup and recovery plans across a wide variety of industries. If you’re ready to start planning your recovery, call us today.


 Preventative Measures
Preventative Measures Detective Measures
Detective Measures Corrective Measures
Corrective Measures
 Determine Recovery Time Objective
Determine Recovery Time Objective Plan for Scalability
Plan for Scalability Check Physical Security
Check Physical Security Check Network Security
Check Network Security List Software Components
List Software Components Determine Facilities
Determine Facilities Clarify Bandwidth
Clarify Bandwidth Automate Backups
Automate Backups Ensure Redundancy
Ensure Redundancy Harden Your Cybersecurity
Harden Your Cybersecurity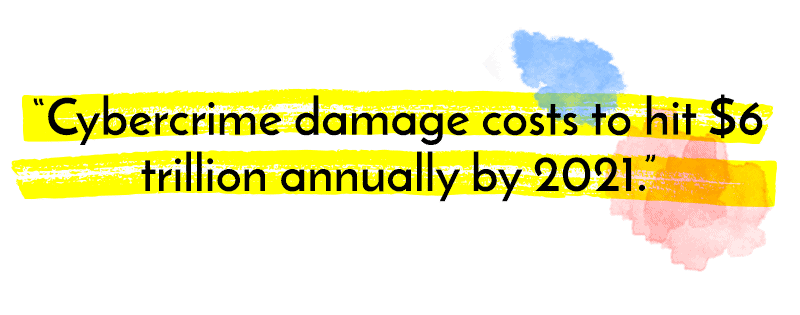
 Do Your Compliance Due Diligence
Do Your Compliance Due Diligence Keep Licenses Current
Keep Licenses Current Establish Key Players
Establish Key Players Create BYOD Program
Create BYOD Program
 Create Scenarios
Create Scenarios Employ Cloud-Based Software
Employ Cloud-Based Software
 Prioritize Restoration
Prioritize Restoration Consider Virtualization
Consider Virtualization Monitor Tests and Usage
Monitor Tests and Usage Test, Test, Test
Test, Test, Test Get Ongoing BDR Support
Get Ongoing BDR Support






