Cybersecurity often shares many comparisons to military and borrows many concepts and terminology from the forces. For example, the Lockheed Martin Cyber Kill Chain is borrowed from a military concept related to the structure of an attack consisting of target identification, force dispatch, decision to order attack, and destruction of target. This Wiki link compares multiple military kill chain models to the cyber kill chain.
More relatable to most businesses these days is the defensive side of the engagement dealing with risk and risk mitigation. Specifically, how to assess and measure risk so that it can be calculated and ultimately reduced to an acceptable level. This is the primary goal of most security programs, after meeting legal and compliance requirements, is to establish a risk assessment program that will reduce risk to an acceptable level via various treatment options such as acceptance, remediation, mitigation, or even transfer.
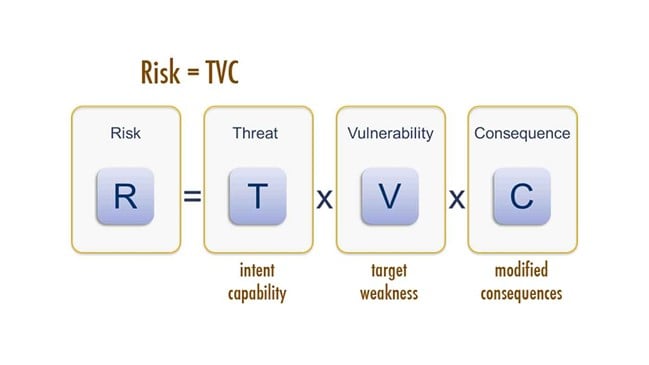
In cybersecurity, a risk is calculated by determining the likelihood that a vulnerability will be exploited and the consequence or impact that it would have if exploited. To continue our comparison to the military arena, I have often relied on the following somewhat blunt analogy to help me keep the various terminology personable and relatable:
I am vulnerable to a gunshot wound. Depending on the munition utilized, placement of the shot, and the consequence (or impact), the wound could even be lethal. Fortunately, my risk remains low because of several factors such as: I live in a small rural area with a low crime rate, and I work in an office building that is secured via many factors. I don’t travel to areas that are considered unsafe. In some way borders help to reduce risk, more to come on this later.
Compare this to an infantry soldier or special forces operative on the battlefield. They are just as vulnerable to a gunshot wound and the consequences would be similar. Their likelihood is considerably higher because of their occupation, location, and assignment. This means their total risk is considerably higher. To reduce this risk to an acceptable level, there are multiple actions taken to mitigate this risk such as: extensive operations training, weapons handling to deter enemies, Kevlar enhanced body armor, bullet proof armor and glass for vehicles, timely threat intelligence, oversight by a central command, allied forces, and much more. This layered defense approach helps protect our critical assets, the solider.
So, let’s transition this back to your business, modern cyber threats, and the digital warzone. I mentioned earlier borders help reduce my risk to gunshot. Unfortunately, in today’s digital landscape there are no borders. Criminal groups like REvil, DoppelPaymer, and HelloKitty responsible for countless ransomware attacks this year alone against companies like Kia – $20M, Acer – $50M, Quanta – $50M, Colonial Pipeline – $5M, Brenntag – $4.4M, JBS Foods – $11M operate in a borderless digital warzone. To ensure we are protecting the critical assets of your business, physical and digital, we must take a similar approach in assessing risk recognizing that our physical location is only a small piece of the attack surface. The digital cyber risk is often much larger and sometimes overlooked. To accurately assess these risks, we need to clearly understand the critical data that we are working with, and where it moves between our organization and customers/clients/partners. Once we have identified the critical assets and the involved people, technology, and process, we can perform a thorough risk assessment to define the vulnerabilities and business impact so we can begin to formulate a plan for reducing that risk to an acceptable level. This will often involve multiple layers of defense, implementing administrative controls for governance as well as training and awareness, investments in technical solutions, partnering with third parties for various items such as cybersecurity controls, insurance, legal assistance, etc.
The goal is to provide a safe environment where we can carry out the mission of our organizations, whether that be on an actual military battlefield, or the borderless digital warzone that businesses operate in today.
Axxys can help better understand your risk profile through our Risk & Vulnerability Assessment process (RVA). Through this process we can establish a current posture for your organization and help layout a roadmap for treating those risk and getting them to an acceptable level. Contact us today to learn more.
P.S. If you liked this one, you may also enjoy our blog ‘Cybersecurity Assessments – Why? Because They’re Good For You, That’s Why…‘